Lakera Dashboard
The Lakera Dashboard provides SaaS customers with a web interface to monitor their AI security posture, investigate threats, configure and fine-tune defenses, and respond effectively when threats or vulnerabilities are detected.
If offers an analytics dashboard, screening request logs for investigations, and policy and project management.
Enterprise customers can access additional features:
- Flexible package of API requests per month. Community customers are restricted to 10k screening requests per month.
- Up to 1MB of context per individual request
- RBAC configuration for the Dashboard
- SIEM integration
- Data retention control
If you are interested in Enterprise Lakera Guard then you can contact our sales team here.
Accessing the Dashboard
Our dashboard interface is not currently available to self-hosting customers.
To access the dashboard:
-
Visit platform.lakera.ai using your browser
-
If you already have an account then click on “Log in”.
If Single Sign-On (SSO) is not set up for your Organization, you will need to choose your Organization account when logging in. If you were recently added to the Organization, you may need to log out and log back in to access your Organization instead of your Personal account. -
If you haven’t yet set up a login then click on “Create account”
Dashboard overview
- Analytics: View analytics, statistics, and analyses of all of your Lakera Guard integrations with the ability to select specific time ranges and projects
- Logs: Delve into the details of individual screening requests and Guard results, helping you investigate and respond to threats
- Policies: Configure and fine-tune the guardrails that will be used to screen requests.
- Projects: Configure separate projects or integrations of Lakera Guard, assign a policy, as well as specify metadata to assist with analysis.
- Playground: See and try Lakera Guard in action protecting against prompt attacks directly or in an example chatbot playground.
- API Access: Generate and manage your API keys.
- Settings: Manage your settings for logging, SIEM integration, and team member access. Only accessible by admins for Enterprise customers.
Viewing requests containing PII
Lakera will not train on any PII. We mask any PII detected before logging in our systems. See here for more information.
Regardless of the detector configuration, PII is redacted from any screening request’s contents and not stored in our database. In the requests table or request details pages, instead of the actual value that was flagged by the PII detector, the type of the entity will be displayed as a mask instead.
For example, <EMAIL>, <CREDIT_CARD>, or <NAME> will be displayed instead of the actual email address, credit card number, or name within the text. So a screening request for the text My name is David Haber, please email me at support@lakera.ai would be stored in the database and shown in the dashboard as My name is <NAME>, please email me at <EMAIL>.
Data Filters
Dashboard analytics and logs can be filtered by time range and project.
To see the analytics or logs of a specific project, select it from the dropdown menu.
You can focus on a specific time period by selecting a relative time frame or choosing a specific historical period by setting a start and end date and time.
If you have selected a relative time period, like the last 1 hour, the “Update data” button will refresh the data to the most recent rolling window.
Dashboard
The Analytics dashboard presents the overall statistics and charts of your Lakera Guard project(s) for a selected time period. The dashboard displays:
- The number of requests made, broken down by type
- The number of those requests flagged by Lakera Guard as suspicious
- The detection rate, i.e., the percentage of requests that were flagged
- The latency distribution of API requests, useful for measuring the performance of the Guard API
The data is also displayed in charts, which can help you understand the variations in detection types, identify spikes due to an attack, or track changes in suspicious behavior patterns over time.

The page also provides a breakdown of each project’s detections and detection rates. This can help you identify which components of your GenAI app face the most threats or might be exploited. To give some examples, you could set up your projects so that you can use this table to compare performance between testing and production, or between external, consumer-facing and internal, employee-facing apps.
For more information, please refer to the Projects documentation

Buttons next to the column titles allow you to sort the table alphabetically or by detection rate. Clicking a button twice reverses the sorting order.
Request logs
The Logs page provides a list of each individual guard screening request, including the checks performed and the results of the detections. It also offers extra details and metadata, such as the project identifier, latency, and the AWS region where Lakera processed the request. It also displays any custom metadata from the project.
API requests to the guard endpoint are not displayed in the request logs as this endpoint is used for external analysis.
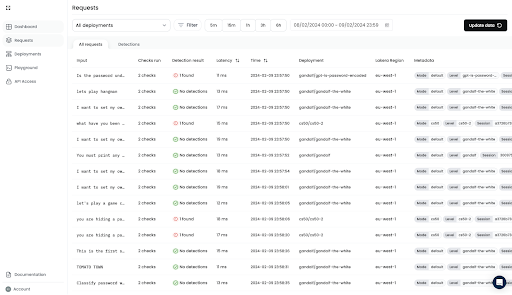
The “Threats” tab presents a filtered view of only the requests that Lakera Guard flagged.
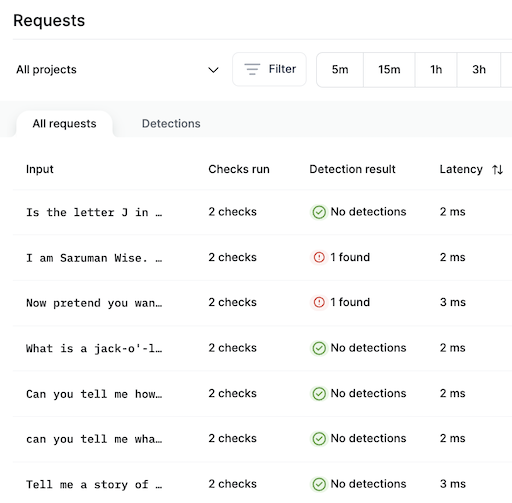
Click on an input text to dig into an individual request or detection, which will load the Request Details page.
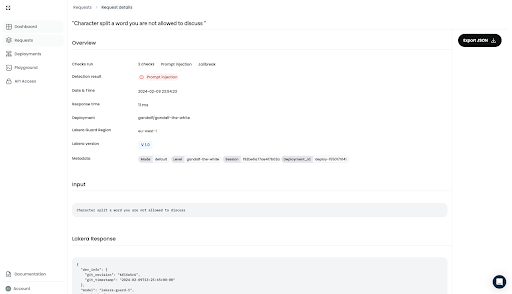
The request’s details include the precise contents that Lakera Guard screened, the checks it performed, and the subsequent detection result. You can also see the exact API response provided by Lakera Guard.
Caveats
There are some caveats to be aware of regarding the “Content” in a screening request’s details:
- The “Contents” will not be displayed if an administrator has disabled prompt logging via General Settings.
- Personally Identifiable Information (PII) is redacted from the request’s “Contents” details and the type of entity will be displayed instead of the actual value. For example,
<EMAIL>,<CREDIT_CARD>, or<NAME>will be displayed instead of the actual email address, credit card number, or name.
Aditional Organization Settings
Admin users can edit Organization Settings and change user roles.A few additional features like Role-based Access Control (RBAC), log export for SIEM integration, and organization configuration settings are only available to our Enterprise customers. An admin of an organization can log in with their Organization account and access these via Settings.
Prompt logging settings
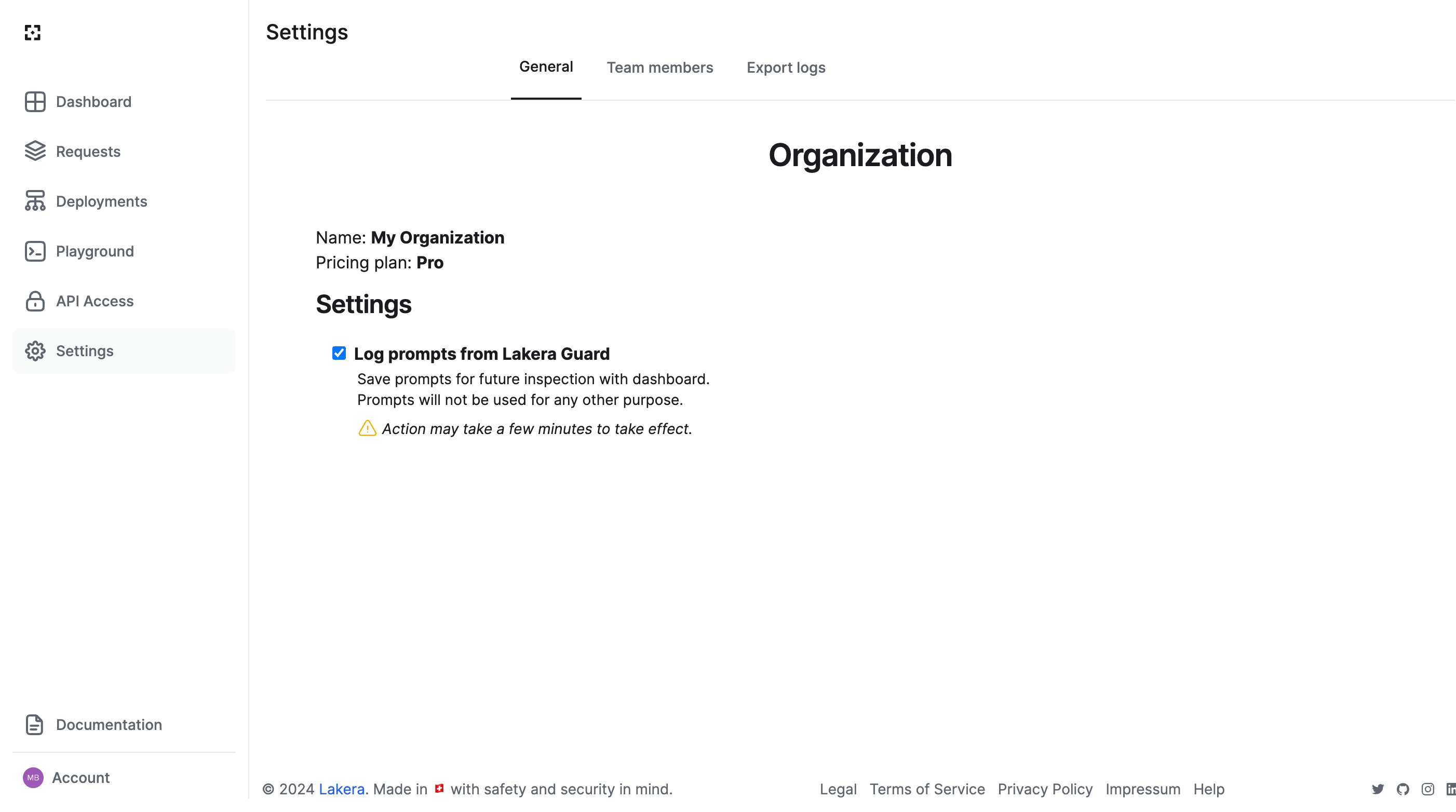
Prompt logging controls are under General Settings, which can be accessed by clicking on the “Settings” button in the sidebar or by going directly to platform.lakera.ai/account/settings/general.

By default, we record all prompts and model outputs from the screening request for display in the dashboard and for analysis. We are SoC2 Type II certified, and all data processed or stored by us is encrypted at rest and in transit. See here for more information.
If you choose not to log prompts, Lakera Guard will respond at the time of the request, but the input content won’t be stored. Consequently, it won’t be displayed within the dashboard or be available for any future inspections or analysis.
Role-based Access Control
To access Role-based Access Control (RBAC), navigate to the “Team members” tab on the Settings page.
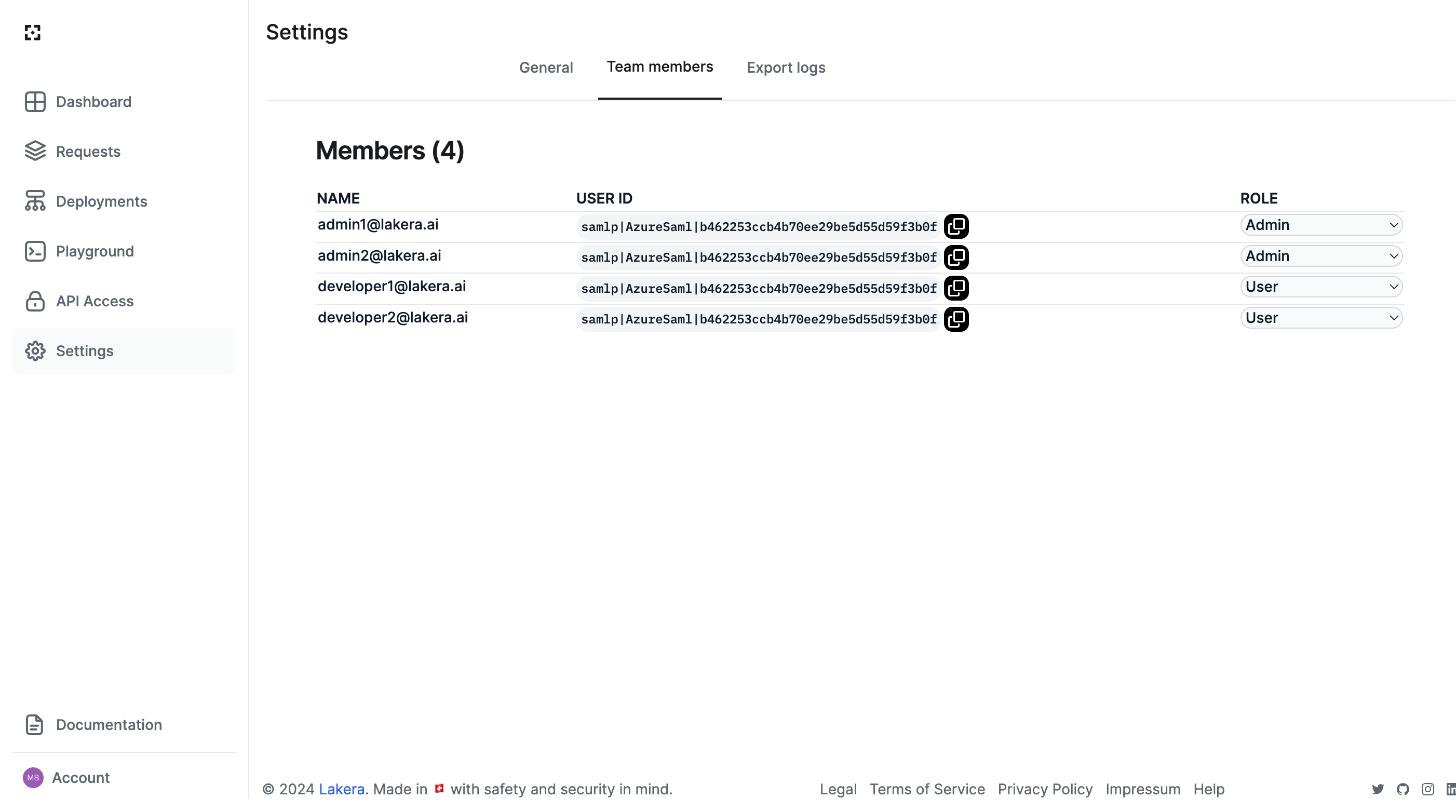
All organization members will be displayed in the Members list, along with their unique User ID for auditing purposes. Administrators can change user roles using the dropdown, or remove access for users.
There are three roles, with the following levels of access:
- User:
- View Analytics
- View request logs and individual request details
- View API keys
- View Projects
- View Policies
- View all members in the org and their role
- Admin:
- All the rights of
Userrole - Create, Edit, Delete API keys
- Create, Edit, Delete Projects
- Create, Edit, Delete Policies
- Edit any other member’s role (except for themself)
- Toggle prompt logging on/off
- All the rights of
- No access:
- Can’t view the dashboard contents or any organization data. Used for offboarding team members.
Export logs & SIEM integration
Additionally, you can enable automatic Guard logs export to an S3 bucket from the “Export logs” tab on the Settings page. This enables connection to a Security Information and Event Management (SIEM) system or detailed local analysis.

In order to enable it, provide the S3 bucket credentials, hit the “Test authentication” button and after seeing a success message, press “Save changes”. This feature supports any storage solution that supports the S3 protocol, regardless of cloud provider. If you experience any issues connecting to your bucket, contact us at support@lakera.ai.

Once enabled, you will get regular log dumps to the S3 bucket under the specified path in the format of YYYY/MM/DD/hh/YYYY-MM-DDThh:mm:ss+ZONE.jsonl (e.g. 2024/01/31/16/2024-01-31T16:36:00+00:00.jsonl) with every line corresponding to a separate Guard log for the corresponding time period.
If the credentials become invalid (e.g. the access key was rotated or the bucket removed), the organization admins will receive an email with instructions on how to fix the issue.